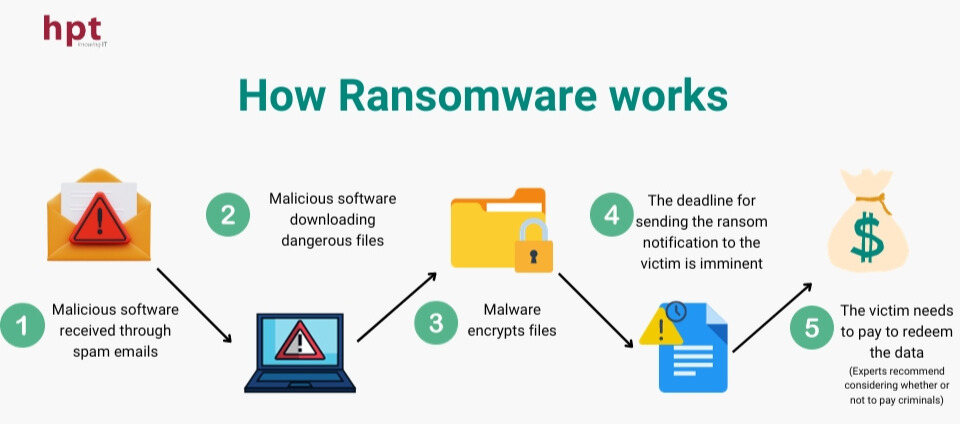
 How ransomware works
How ransomware works
3. Types of Ransomware
- Crypto Ransomware: This is the most common type, encrypting crucial data and demanding a ransom for decryption. This attack can cause significant loss without data backups.
- Locker Ransomware: Primarily locks the user's screen and demands a ransom to unlock it. While it doesn't encrypt data, it completely disrupts computer usage.
- Scareware: Generates fake computer issue notifications to trick users into downloading malicious software. This is essentially an intrusion from "within."
- Malvertising: Uses online ads to install malware on computers without prior user notice.
- Human-operated Ransomware: This is a new trend, targeting organizations by infiltrating and deploying ransomware across enterprise networks. These are often well-prepared and carefully planned attacks.
- Ransomware as a Service: Provides attackers with ransomware "services," making it convenient to conduct attacks without deep technical knowledge.
4. Notable Ransomware Attacks
- DarkSide: The most notable attack causing chaos in the U.S. energy supply chain, compelling Colonial Pipeline to pay a $4.4 million ransom.
- EvilCorp/CryptoLocker - Attack on CNA Insurance: Inflicted severe damage by encrypting over 15,000 devices, including remote employees' computers.
- REvil/Sodinokibi - Attacks on Quanta, JBS Foods, and Kaseya: Demanding large ransoms, resulting in significant consequences for major companies and the food industry.
5. Preventing and Containing Ransomware
- Use cloud-based protection tools: Cloud-based backups to safeguard data and facilitate quick restoration when needed.
- Train employees in cybersecurity: Educate staff on ransomware prevention methods, emphasizing the identification of malicious emails.
- Regular system updates: Update software and systems frequently to prevent security vulnerabilities.
- Use secure email: Implement secure email solutions to block harmful file attachments.
- Offline data backups: Ensure offline data backups to protect against ransomware.
- Implement robust identity security measures: Employ identity security measures to enhance resilience against ransomware.
6. What to Do When Attacked by Ransomware?
- Identify infected systems: Locate and isolate affected devices to halt the spread.
- Prevent further spread: Immediately disconnect networks and infected devices to stop the spread.
- Assess damages: Determine the impact on systems and data.
- Check backups: Restore data from previously created backups before the attack.
- Report the attack: Report the incident for support and better post-attack management.
7. Ransomware Prevention Solution from Yubico
Yubico offers a ransomware prevention solution through the use of YubiKey - a passwordless authentication device. Ransomware typically encrypts system data and demands a ransom for decryption. Combining YubiKey with robust authentication systems is an effective way to counter this type of attack.
Reused passwords, weak passwords, SMS, OTP, or weak multi-factor authentication solutions based on applications are often the root - or at least a considerable contributor - to ransomware attacks. Strong phishing prevention solutions like hardware-based authentication provided by YubiKey can help organizations avoid using easily tricked authentication methods for any accounts.
The best defense against ransomware starts with modern phishing-resistant protocols like FIDO2/WebAuthn and FIDO U2F. YubiKey not only supports new authentication protocols but also integrates with legacy authentication forms like One Time Passwords (OTP), enabling organizations to transition easily without entirely overhauling their current infrastructure.
With nearly 30 years of experience in IT, HPT is an official partner of Yubico in Vietnam, supplying genuine YubiKey products. This is a robust authentication method that enhances security and minimizes the risk of ransomware attacks. The combination of the powerful authentication solution YubiKey and HPT's deployment expertise promises safety and reliability for organizations in preventing and mitigating these harmful attacks.