THE IMPORTANCE OF INFORMATION SECURITY
In today's highly competitive information-driven era, information has become a vital asset for any organization. Building an information security system and creating an effective defensive shield for an organization's entire strategies and operations from external and internal threats, has become a top priority for many organizations. Consequently, factors closely related to information security, such as people, processes, data, and technology, need to be thoroughly considered. Establishing safety standards from the outset is essential to lay a solid foundation for development, adopt modern technologies, keep up with trends, bring about improvements, reduce costs, and shorten the time to market for businesses and organizations.
Based on these priority factors, HPT has conducted research to implement a comprehensive information security consulting model for organizations and businesses in Vietnam. This model includes the most comprehensive solutions and services, ranging from hardware and software to professional security consulting services, to address all security challenges within organizations. It not only helps ensure information security but, more importantly, ensures operational efficiency, bringing significant added value and laying the foundation for business development.
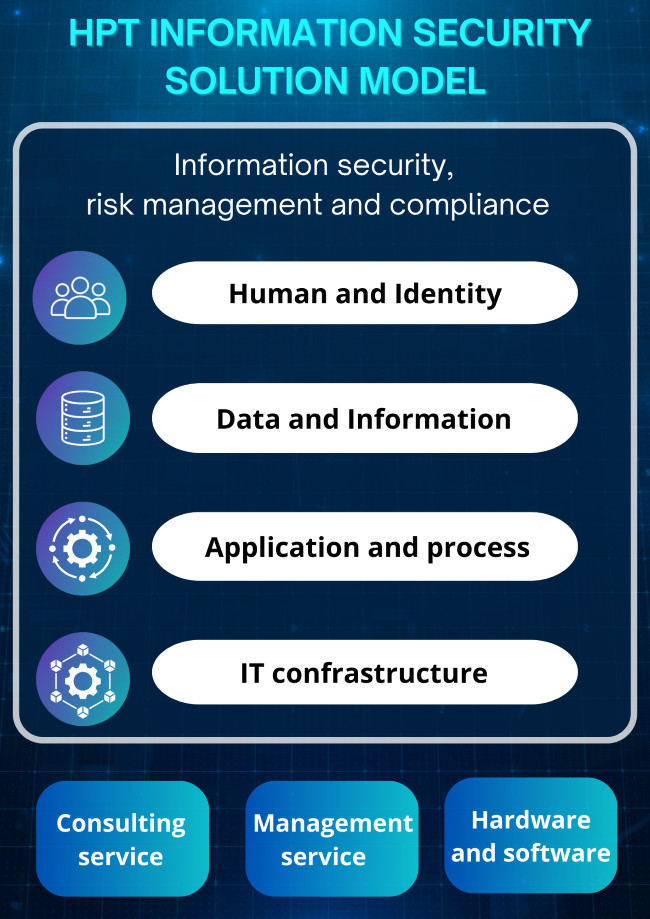
Information security, risk management and compliance
INFORMATION SECURITY SOLUTIONS
Information security, risk management and compliance
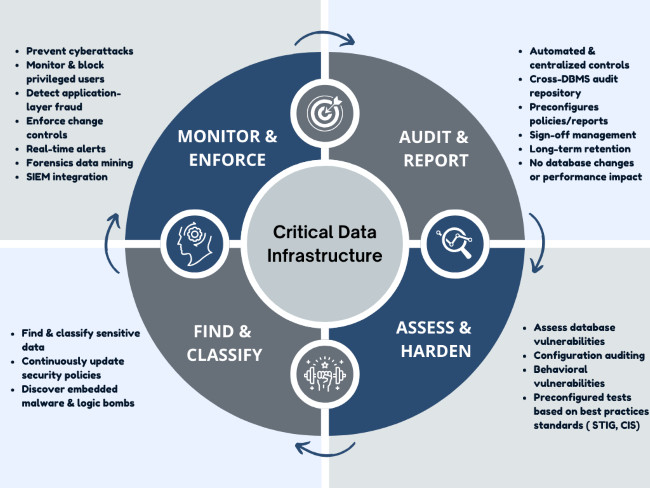
With a robust technology platform that increasingly develop and expand, mornitoring security information within the system is truly necessary. This helps in overseeing a system with numerous diverse components being managed, provided centralized alerts, automatically analysis and assessment for each component as well as the whole system. Furthermore, monitoring allows for correlation and chaining events from multiple systems to provide an accurate information flow from attacks, thereby identifying their origins and offer timely remedial actions.
In addition,the Information Security solution allows for measuring, managing risks, and overseeing compliance with critical business processes to bringing effective results:
+ Identifying security issues and giving the time for solving information security incidents by collecting data from all technology platforms, software, and applications. Correlating events with various contexts, scanning for serious incidents, and simultaneously monitoring user’s behaviors to detect internal threats.
+ Providing compliance reports for IT systems based on international standards such as ISO 27001, PCI-DSS, NIST, etc., automatically or whenever required by the organization. Managing incidents and organizing events across the entire system with a more user-friendly, unified, and efficient interface.
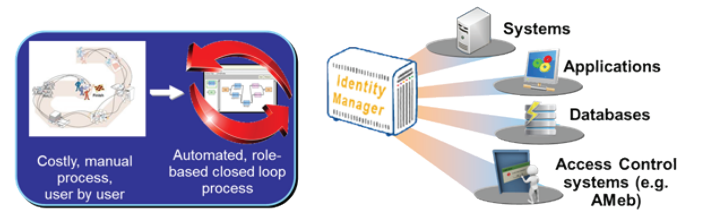
Accounts, customer information, transaction passwords... are highly confidential information. Therefore, managing and monitoring the storage of such information is particularly crucial. Clearly, attackers often do not steal individual accounts or passwords but typically use administrative accounts, privileged accounts to easily steal large amounts of confidential information. Therefore, ensure that your business's information technology system is maximally secure against such attacks.
Implementing the management solution for identity, privileged account, and access helps businesses:
+ Align with compliance standards: High security is the technology key that helps businesses and organizations achieve international standards in information security, instilling confidence in customers and business partners.
+ Improved business efficiency: Enhance compliance in production and business operations with just one access point to sensitive assets and automated management of privileged access accounts.
+ Easy management of application access (hardcoded, embedded credentials) across various hardware, software, and virtualization environments.
+ Isolate and protect critical IT assets from administrative users, endpoints infected with malware, backdoors, etc.
+ Report compliance with Sarbanes-Oxley, PCI, and Basel II standards for the enterprise's information technology system.
+ Minimize external and internal threats: Control administrative users' access to highly sensitive assets, define and enforce consistent security policies for managing the privileged identity of the entire system.
+ Controlling real-time of all administrative sessions, in encrypted video format.
Data and Information
According to statistics from the major security organizations like Trustwave, TrendMicro, and the research organizations like Gartner and Forrester, etc., there is an increasing number of attacks on information technology systems. Over 80% of these attacks target the data and critical information of businesses, and the trend of hackers is gradually shifting from destructive purposes to financial gains. Bank is one of vital components of the economy, and always at the forefront of applying information technology systems in their operations, also making it becomes “big targets” for attacks.
+ Data and information security management solutions will provide businesses with the ability to monitor and manage data in real-time, centralized monitoring, allowing businesses to search and categorize important information, thereby providing policies based on user’s behavior.
+ The solution offers multiple instant alerting methods when policy violations are detected, such as Email, SMS, SNMP, SIEM, etc., enabling businesses and organizations to proactively protect data and critical information against these dangerous attacks.
+ Additionally, the organization's information and data are evaluated and reported according to current popular security standards such as SOX, PCI-DSS, HIPAA...
+ Furthermore, current data and information management and monitoring solutions also establish workflows within an organization. These workflows operate according to pre-set schedules or Administrator's purposes. Business management at each level will periodically receive reports on application activities into the database, reports on violation behaviors, and requests to be executed according to predefined procedures. The solution will monitor the execution of these processes and provide the general summary reports, assisting businesses in successfully passing audits and achieving clear management effectiveness.
+ There are multiple deployment options available to customers for data loss prevention and information management solutions. Deployment can be done without impacting the end users or the current system operations, ensuring quick and convenient integration capabilities.
Applications and Processes
Businesses need to proactively protect their critical production and business applications from internal and external threats throughout the entire lifecycle of the application, from design to implementation and operation.
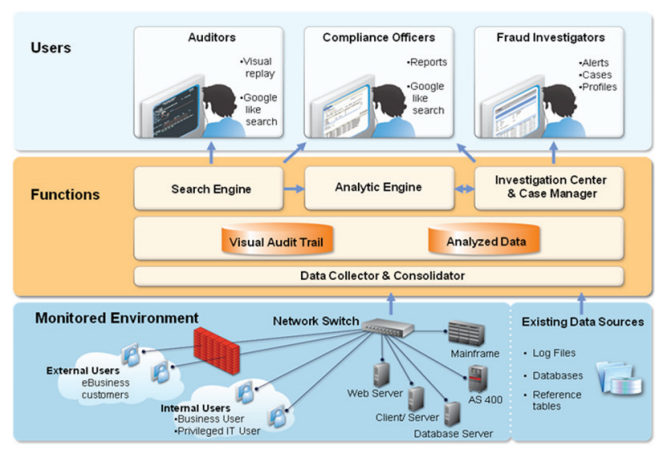
The Centralized Application Monitoring solution is suitable for many businesses, especially those in the banking and finance sectors. This solution records all activities in the enterprise's application system and provides administrators with the ability to monitor, analyze multidimensional data, and give the real-time alerts upon detecting abnormal behaviors or violations in the system.
In the process of developing and operating application systems, businesses also need to focus on building support processes to handle system failures. Automating operational and administrative processes, as well as incident handling, will ensure continuous and full-time control of the system, optimizing efficiency, and minimizing risks for the core activities of the business.
+ The Centralized Application Monitoring solution provides businesses with the ability to monitor their applications operating across multiple platforms, programming languages, and various types of applications. Especially, the solution supports specialized applications for banking such as ATM, Internet Banking, Finance, etc.
+ The solution combines powerful monitoring capabilities, gathering information from various sources such as SSH, HTTP, databases, shared information, to analyze and evaluate violations. It then generates specific reports that allow administrators or investigators to review all alerts, violations, or detailed profiles of each relevant subject.
+ Detect and enforce the enterprise's security policies, identifying violations in invalid transactions of ATM, Internet Banking, and specialized transactions in finance, credit, and manufacturing sectors.
+ Enable the recreation of past transactions, accurately determining what actions the service users performed.
+ Monitor the activities of business processes, track process compliance, and evaluate and manage potential risks. Additionally, classify processes according to criteria specified by the business.
+ Operate the application system, monitor, and handle incidents easily, centrally, and automatically.
Securing IT infrastructure is a crucial component of a business's information security foundation. A robust IT infrastructure provides the foundation for developing new systems and applications that effectively support business and production.
Protecting a business's infrastructure involves preventing damage and loss of physical infrastructure, safeguarding against indirect threats and vulnerabilities such as the loss of a utility service, lapses in physical access control, or the loss of critical physical components. Effective security requires a centralized management system that correlates different input factors, including assets, employees, customers, and more.

SUCCESS WITH HPT
At HPT, we strive continuously to research comprehensive and in-depth security models, offering new solution directions along with advanced technology trends. HPT always aims to collaborate with customers to build a robust security foundation for their information technology systems, ensure the efficient business processes, address the challenges of developing new business models, expanding globally, and meeting the increasingly stringent requirements for information safety and security.
Some notable customers who have used the security solutions and services provided by HPT:
Some clients operate in the fields of Finance, Banking, Government, and other agencies:
To deliver comprehensive solutions in information security and system security, as well as transfer the best technology to our clients, HPT has built a team of consulting experts, deployment engineers, and project managers specializing in all areas of information security. HPT is currently a premier partner of many leading global security solution providers such as Cisco, Checkpoint, HP, IBM, Oracle, etc. Additionally, with over 18 years of experience in system integration and software development, HPT is confident in addressing any issues related to connectivity, compatibility, and work performance… in consulting, designing, and deploying information security solutions for our clients.