Penetration Testing Service
 |
|
| HPT provides Penetration Testing services to assist organizations and businesses in effectively and efficiently addressing cybersecurity challenges. |
|
| The primary service categories |
|  | |  | |  | |
| Services publicly accessible on the internet include: Web, Mobile, API, Email, … | |
Network systems, servers, workstations, defensive devices, Active Directory systems | | Firmware, IOT systems, Cameras, SmartHomes | |
| | | | | | |
|  | |  | |  | |
|
Automation systems (audit) | |
Cloud Pentest | |
Source code security testing | |
| | | | | | | | |
|  | | Maintaining and ensuring trust with customers, partners, and confidential business data. 
| | |  | | Identifying vulnerabilities against external attackers, minimizing information asset loss, ensuring and sustaining business operations. 
|
| | | | | | | | |
|  | | Effectively leveraging defensive solutions and optimizing IT investment efficiency.  | | |  | | Meeting Industry-Specific Requirements or International Standards such as PCIDSS, GDPR, ISO 27001.

|
|
| | | | |
| | |
| International Standards Application |

|
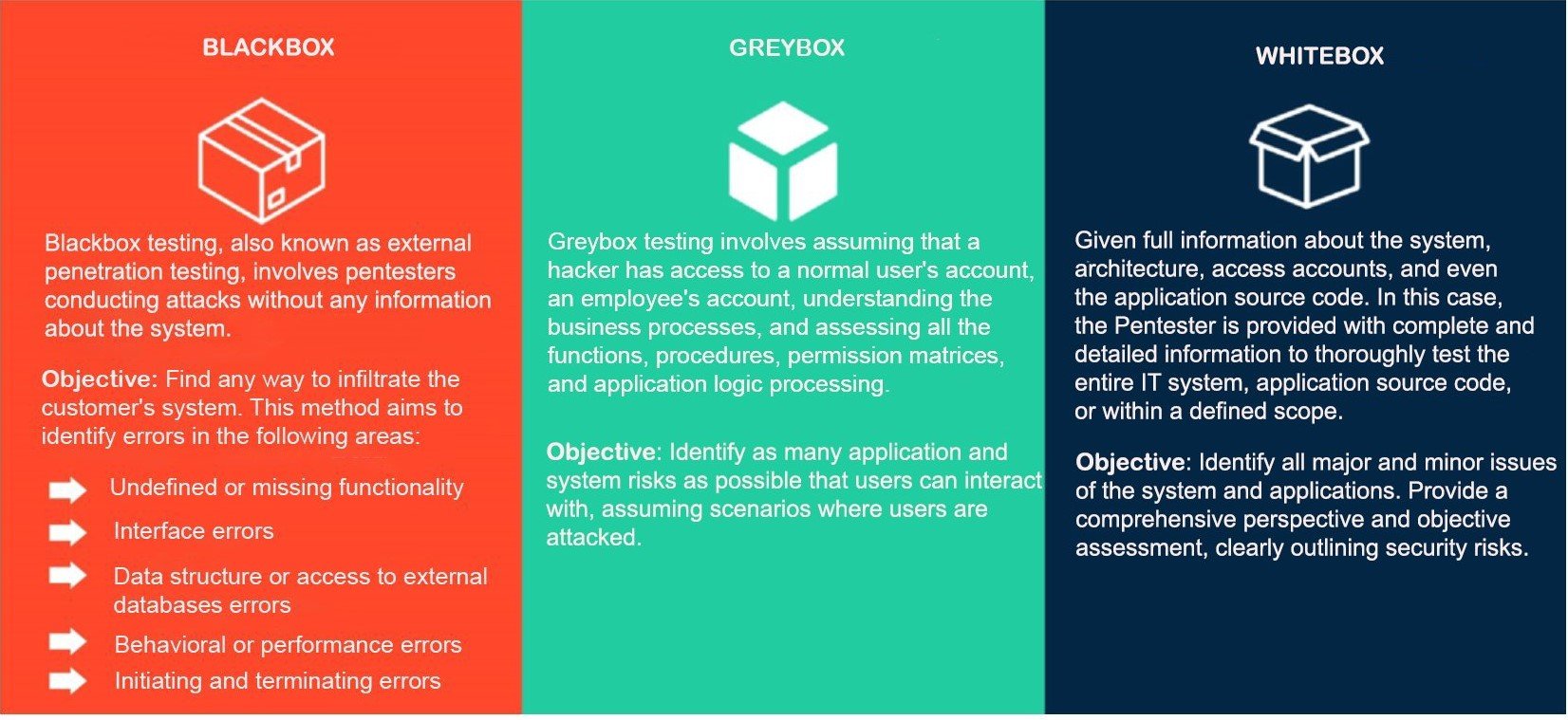
Assessment Methodology |
|
| Pentest Web & Mobile |
List of tasks involved in Web & Mobile assessment: |
| List of tasks for Web assessment | | | List of tasks for Mobile assessment | | | | | |  | Information Gathering | |  | M1: Improper Platform Usage | | | | |
|  | Configuration and Deploy
Management Testing | |  | M2: Insecure Data Storage | |
| | |
|  | Identity Management Testing | |  | M3: Insecure Communication | |
| | |
|  | Authentication Testing | |  | M4: Insecure Authentication | |
| | |
|  | Authorization Testing | |  | M5: Insufficient Cryptography | |
| | |
|  | Session Management Testing | |  | M6: Insecure Authorization | |
| | |
|  | Data Validation Testing | |  | M7: Client Code Quality | |
| | |
|  | Error Handling | |  | M8: Code Tampering | |
| | |
|  | Cryptography | |  | M9: Reverse Engineering | |
| | |
|  | Business Logic Testing | |  | M10: Extraneous Functionality | | | | | |  | Client-Side Testing | | | |
|
| | | |
|
| Result and value brought by the service |
The detailed report provides specific and comprehensive results for each assessed content. For each detected vulnerability, engineers provide a clear and visual representation of the findings: |
| | | | | | | | |
|  | | Detailed description of vulnerabilities. 
| |
|  | | Details of the steps taken to successfully exploit the vulnerability.  |
| | | | | | | | |
| 
| | Impact of vulnerabilities on the system. 
| | |  | | Recommendations for addressing the vulnerability. 
|
| | | | | | | | |
The impact level of each vulnerability is accurately assessed based on the Common Vulnerability Scoring System (CVSS), which is built upon 6 criteria: |
|
.jpg) |
| The first three criteria assess the exploitability of the vulnerability, while the latter three assess the impact of the vulnerability. Based on the CVSS scoring system, engineers accurately determine the level of impact for each vulnerability using corresponding score scales, and visually represent the decreasing impact levels of each vulnerability in the report, including Critical, High, Medium, and Low. |
|
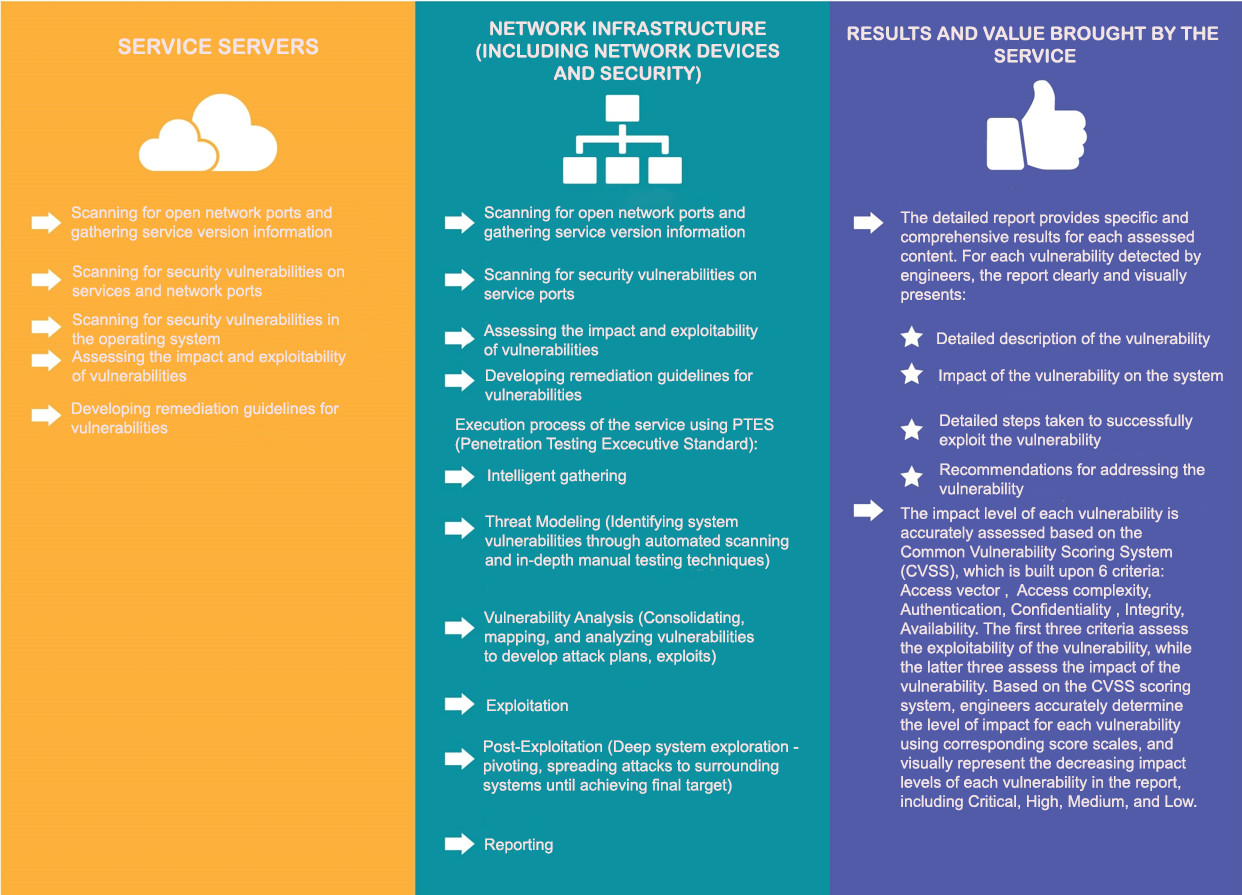
| Pentest System/Network |
|
The Network Penetration Testing is conducted by integrating international system assessment procedures such as ISSAF, OSSTMM, PTES, and the security assessment process of ECCouncil. These procedures are implemented by the HPT assessment team and tailored to the scope provided within the service package. |
 |
|
| Conclusion |
 | Penetration testing (Pentest) is the process of simulating the entire attack process on an ICT system by creating network attack scenarios to identify security vulnerabilities that attackers could exploit to gain control or launch targeted attacks, such as ransomware attacks. | | | 
| In addition to discovering exploitable pathways and deep system attacks, Pentest also reflects the effectiveness of security technologies in the system by identifying existing security vulnerabilities in the defense solutions deployed. | | |  | Pentest services provide organizations and enterprises with a comprehensive overview of these weaknesses to promptly devise remediation plans. Consequently, businesses can enhance the efficiency of their security technologies, establish a roadmap for upgrading security systems, and focus on business development with peace of mind. | | |  | ICT systems cannot maintain absolute security over time and always have vulnerabilities and risks that may be exploited with the development of cyberattacks. Therefore, to mitigate and minimize these risks, organizations and enterprises should conduct pentests at least every six months or once a year with a professional and independent service provider. |
|