HPT SECURITY AUDITING SERVICE
 |
|
HPT provides Security Auditing services to enhance security, check configurations on each object, helping organizations and businesses optimize their existing resources and strengthen the security of their systems. |
|
| | The implementation standards | | |
| | | | | |
.png) |
|
| Benefits |
Unlike penetration testing, this service proactively checks security configurations from a system administration perspective, verifies and maintains vulnerability patches, and then provides Pass/Fail criteria, recommends optimal solutions, and fine-tunes security configurations aim to: |
|
| | | | | | | | |
|  | | By adhering to CIS standards, this service reduces the risk of attacks exploiting misconfigurations during systems operations. 
| | |  | | Proactively optimize and refine security configurations, strengthen the entire cybersecurity system, minimize the risk of single-point attacks and lateral movement attacks. 
|
| | | | | | | | |
|  | | Maintain and ensure configurations and vulnerability patches for the entire system.  | | |  | | Improve security within the system to ensure business operations.

|
| | | | | | | | |
|  | | Enhance the process and periodicity of security checks and maintenance.  | | | | | |
|
| | | | |
| | |
| Implementation Method |
| Assessment Team will set up the evaluation environment and tools within the Customer's internal network environment, then proceed to utilize administration accounts, connecting from the assessment server to the evaluated objects through the network. The assessment process comprises the following steps: |
.png)
|
|
| Assessment Criteria |
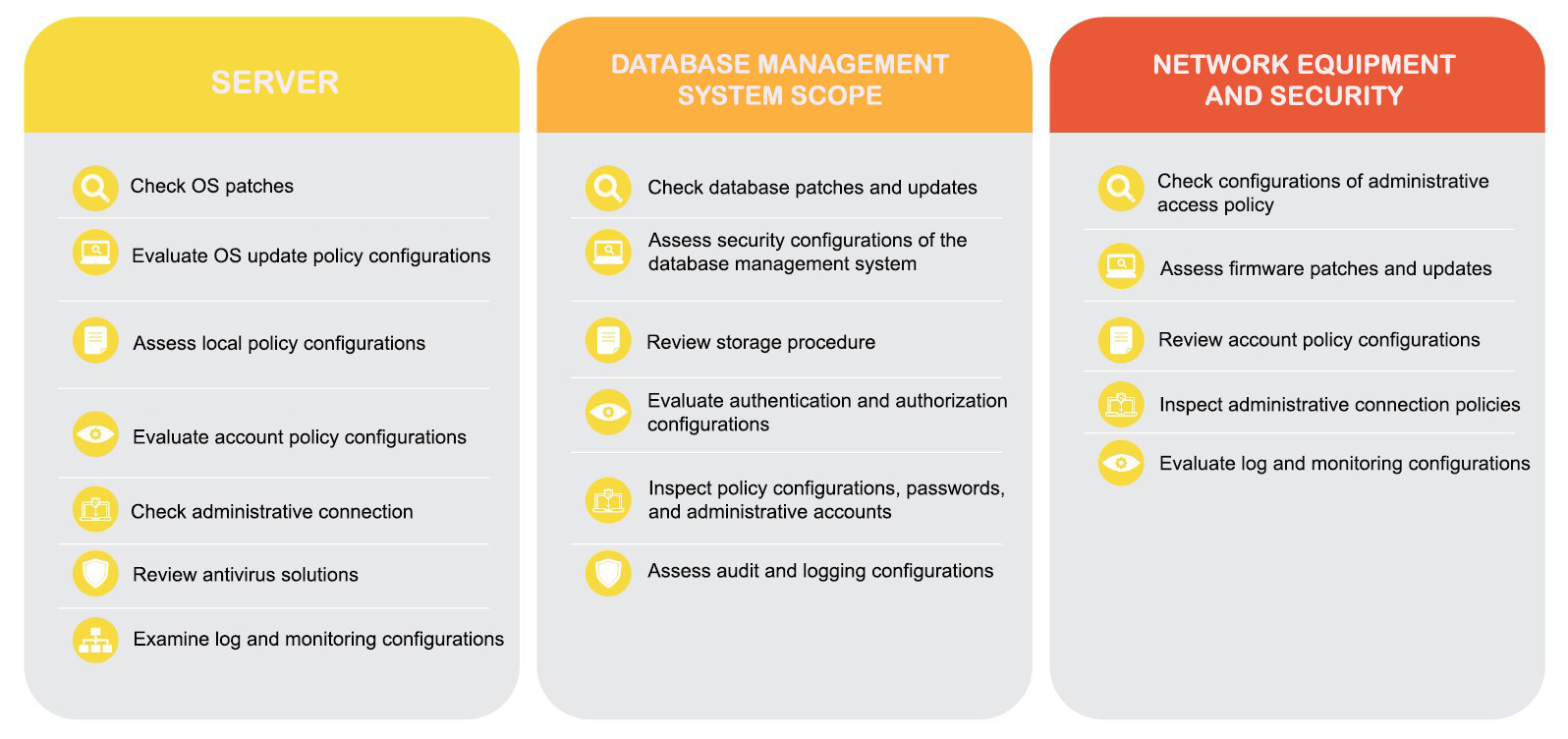
|
|
| Conclusion |
| During the development, operation, and provision of services, the IT systems of enterprises are often deployed either through self-build or by hiring deployment units. Most initial configurations are typically set up just to get systems running, and information security is often overlooked, leading to misconfigurations taht can lead serious consequences later on. Understanding the systems and assets of our customer, HPT will conduct security configuration assessment according to CIS standards to ensure that the IT assets of enterprises, including operating systems, databases, and network devices, comply with international security standards. According to CIS, any system adhering to CIS Benchmarks will mitigate most system threats and reduce risks posed by human factors. | | |
|