• Scan for abnormal files on disk
• Detect abnormal processes, services, task schedules
• Scan for applications that automatically launch with the system.
• Scan for anomalies, IOCs on memory, on disk, and on I/O connections on the server.
• Check the software versions installed on the server, referencing the disclosed vulnerabilities against the Exploit-DB database.
• Check the configuration information for GPOs policy based on CIS standards.
• Examine the events recorded in the Windows Eventlog, correlate and detect anomalies based on predefined rule sets.
• Deployment method can be done on each server or deployed simultaneously on a range of servers provided without having to install agents on the server.
• Support both deployment in Airgap environment, isolated networks, or through one-way Firewalls such as Data Diode, HPT Mavex can deploy and provide clear results.
Scan for abnormal files on disk
HPT Mavex relies on key factors to detect files with unusual signs that exist on the system. Consists of:
· Based on the YARA rule set, HPT Mavex scans the predefined ranges to detect anomalies in Windows components such as processes, services, Task Schedule, Registry, Startup. This Yara Rule is continuously researched and updated by HPT Cyber Security Team.
· Based on a hash database of files on Windows systems on various versions. Analyzed on Sandbox platforms, Threat Intelligence from more than 60 sources around the world, internal IOC from HSOC (HPT SOC), .. before being labeled and built into a database for use. At the same time, applying Machine Learning in identifying malicious code, suspicious signs.
· Based on the source information attached within the Meta Data of the files. Files that do not have all the basic information of a file will be collected.
· Based on the connections and execution history of the above set, the traces collected on each object, the collected information to support the identification results.
Check for software vulnerabilities installed on the system
The programs installed on the server are collected, analyzed and evaluated based on the version, on that basis, determining the corresponding vulnerabilities that may exist on the version being used. Provides an overview of attack surfaces related to software and applications installed on the server.
Check the GPO policy configuration information
The GPOs policy information configured on each server is collected by HPT Mavex and then evaluated against criteria developed by the CIS. The evaluation criteria are drawn from the standards corresponding to different operating systems, then, are reduced to the most basic and necessary standards. Mavex based on those standards, will collect, analyze, evaluate and give pass or fail results for each criterion. At the same time, it also outlines a specific adjustment plan, filtered from the CIS Benchmark, to specify the tasks that need to be done for the manager.
Check events logged in Windows Eventlog
System events logged and stored by the Windows Eventlog will be collected by HPT Mavex, correlate each single events, into sets of interrelated events on the system. From the above sequence of events, we build rule sets to detect and identify the above sequence of events that are likely to be similar to forms of attacks on the system. Identifiable attacks such as:
- Suspicious account behavior
- Command line/Sysmon/PowerShell auditing
- Service auditing
- Credential Dump
User interface
To help organizations achieve the overall security monitoring picture, HPT Mavex provides a diverse visual main monitoring interface.
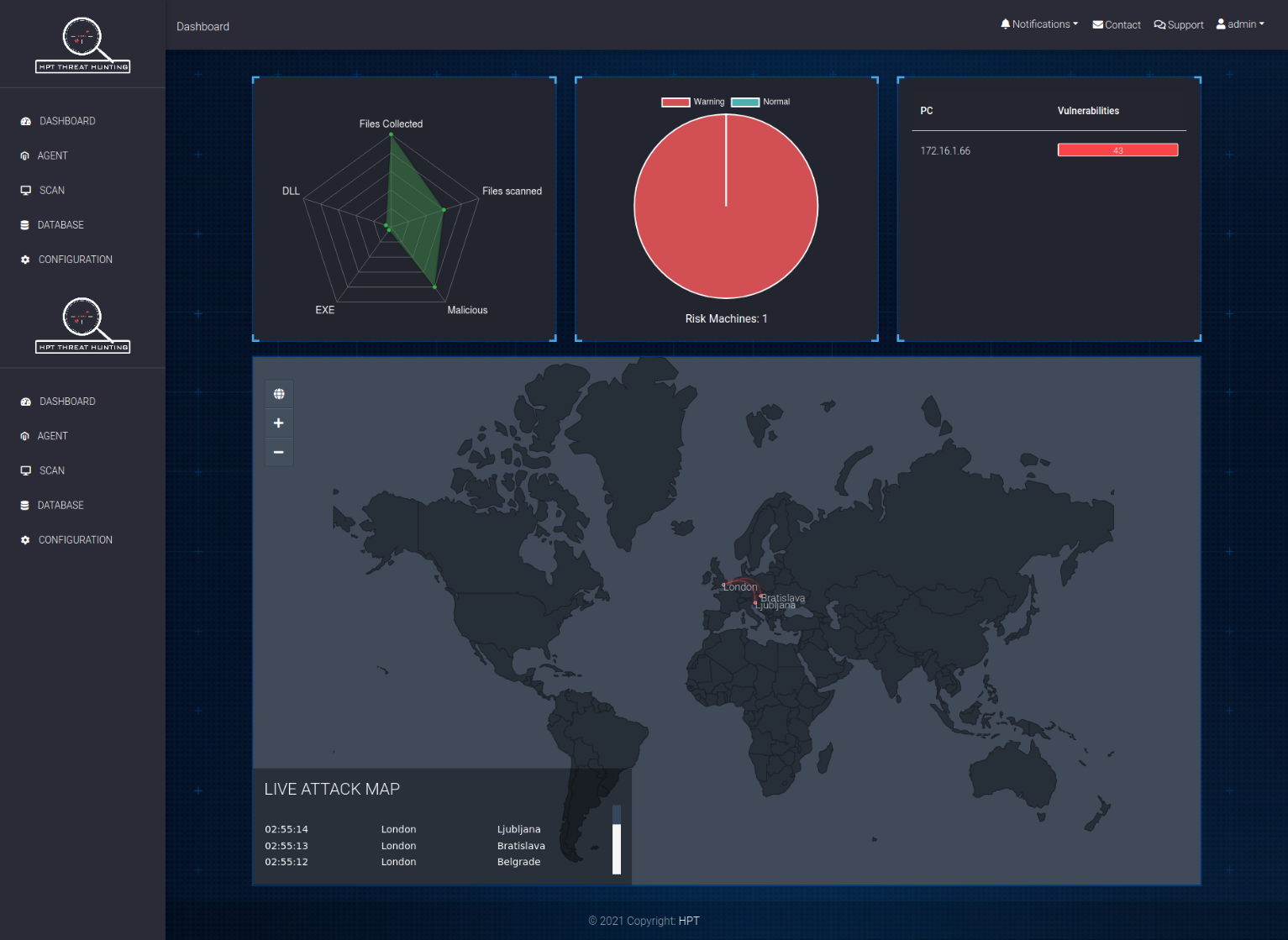
Overall interface image of HPT Mavex
· The interface is hierarchical according to each server, each server represents information specific to each of those servers.
· The monitoring interface is built according to user-friendly criteria, representing the full range of Windows components in an intuitive, easy-to-follow manner.
· Visualize the assets collected and the results after analysis.
· Allows exporting reports in different formats PDF, HTML...
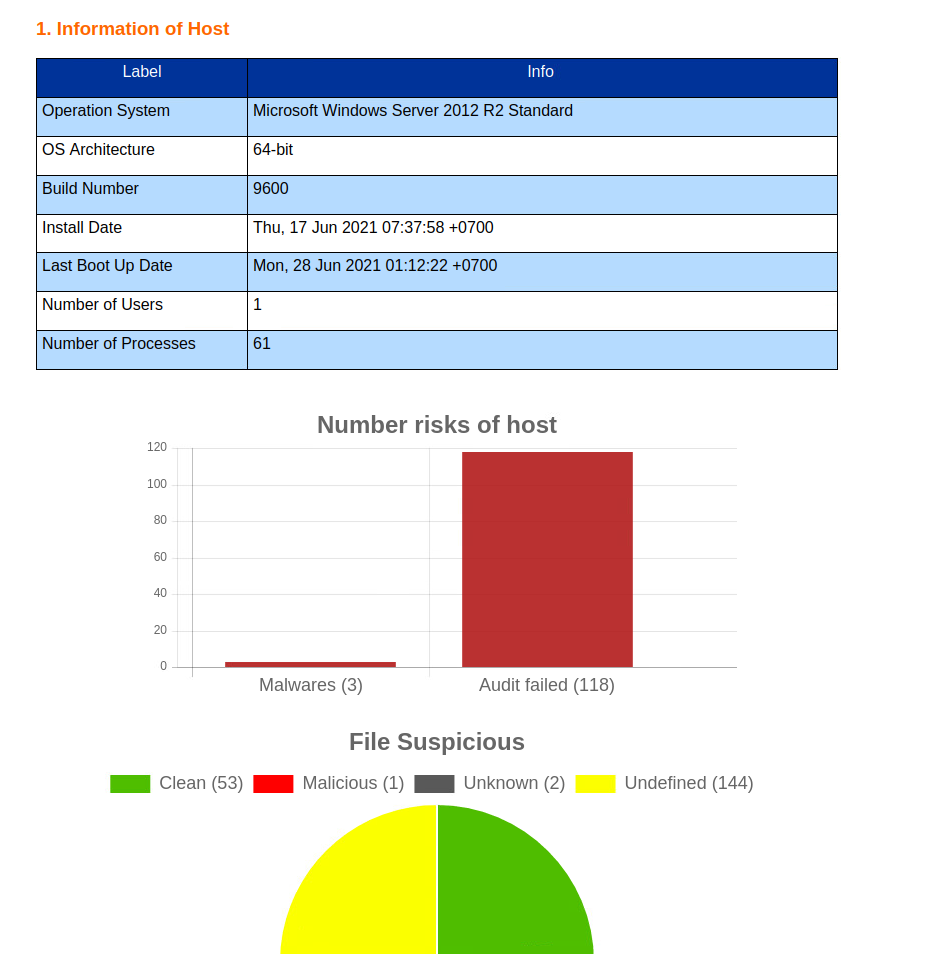 HTML report image published by HPT Mavex
HTML report image published by HPT MavexDeployment model
HPT Mavex supports deployment in 02 main models, suitable for the characteristics of each system such as:
· Cloud-based deployment: support for servers, the system of servers can access the internet. In this model, customers will be provided with agents to execute on the required servers. The advantage of this model is that it is quick to deploy because the system is already available, just receive the Agent and execute it on each server unit.
· On-premise deployment: support for customers who do not need to use cloud-based or specific systems that do not have an external connection to the Internet. Deploying this model requires some preparation time before threat hunting to be able to deploy the onpremis analytics server. The advantage of this model is that all customer data is stored on the customer's system. Solve the problem of limiting internet access to important servers or the entire system.
Product is certified by Copyright Department
